Redesign Of Anomalies Presentation
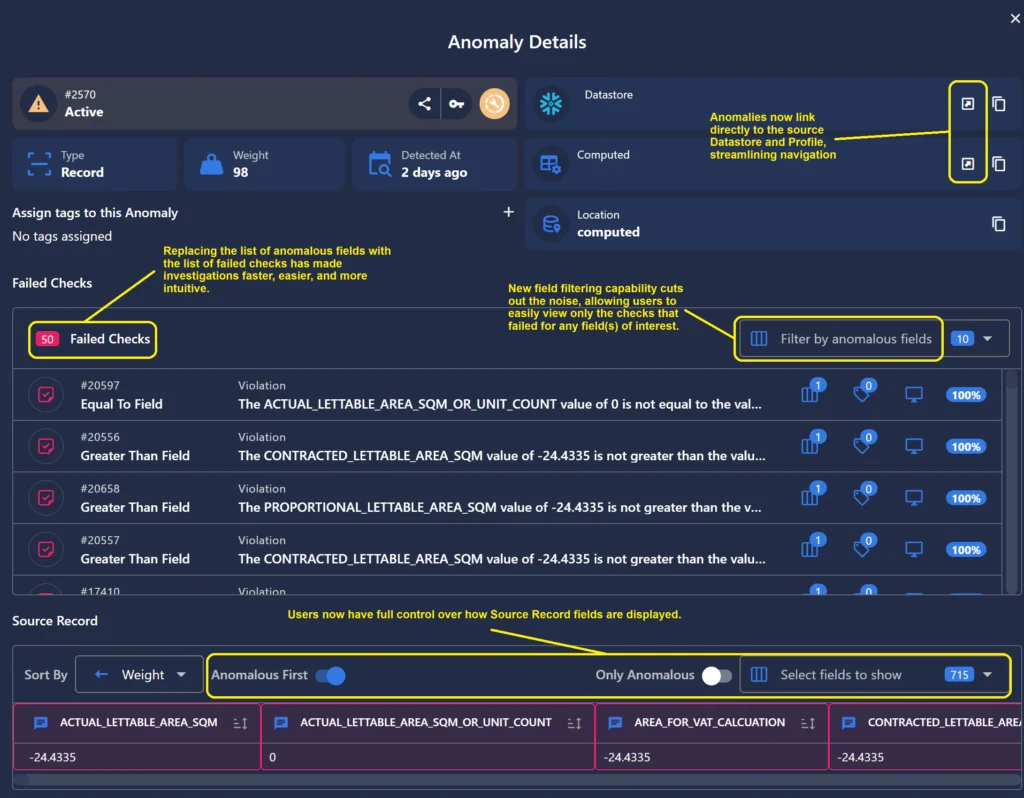
- Previously, the Anomaly modal presented the user with a list of all anomalous fields, each of which referenced the corresponding failed checks and the specific violations thereof. This required the user to interrogate each listed field individually in order to completely understand the specifics of why those fields were flagged as anomalous, resulting in a very tedious process if more than a handful of fields were present. In the redesigned Anomaly modal, we instead present the user with a list of all of the failed checks, and group all fields that are in violation of the same check together. This results in an easier, faster, and more intuitive user experience when analyzing failed checks and their associated anomalous records.
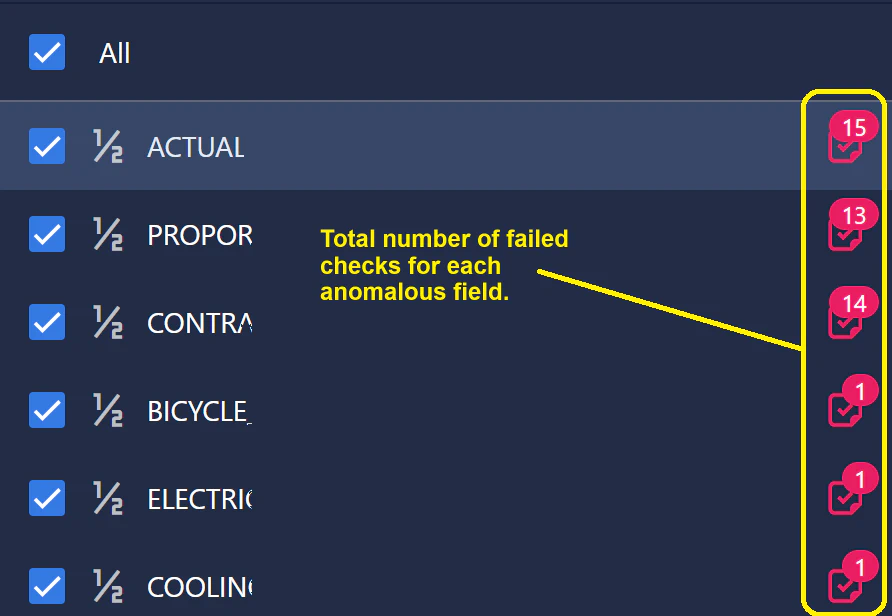
- Next, we have made this list of failed checks filterable via an Anomalous Fields picklist, allowing the user to instantly identify which check(s) failed for a given field.
- Within the picklist view, we also display the total number of failed checks per field, helping users to quickly identify which fields may need to be prioritized for analysis.
- We have created a direct link between the Anomaly interface and the Anomaly’s source Datastore and Profile, allowing for seamless navigation to these related pages.
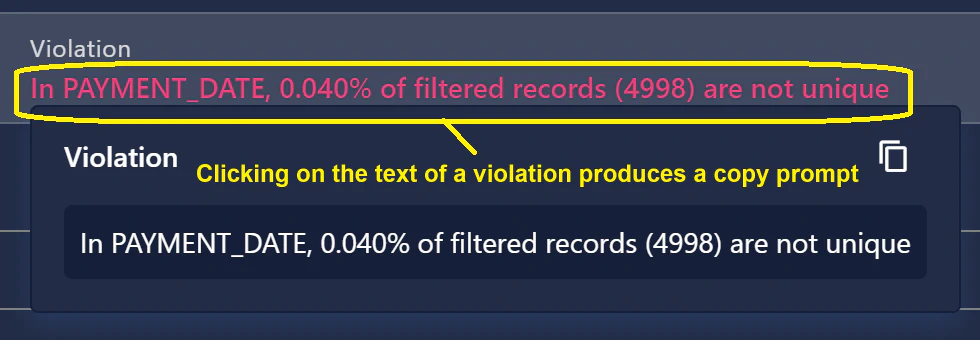
- Based on client feedback, we have added a click-to-copy feature that displays when a user clicks on a failed check’s violation description, allowing the user to quickly share anomaly details without exporting data.
- Users now have more control over how Source Record fields are displayed. They can select “Anomalous First” to move anomalous fields to the front of the line while still viewing all other fields, “Only Anomalous” to view only fields that have identified anomalies, or use the searchable picklist for a fully customized view.
- Tag management within the Anomaly interface has been reformatted with a more user-friendly display.
We look forward to your feedback!
Multi-Select Actions Now Include Operations
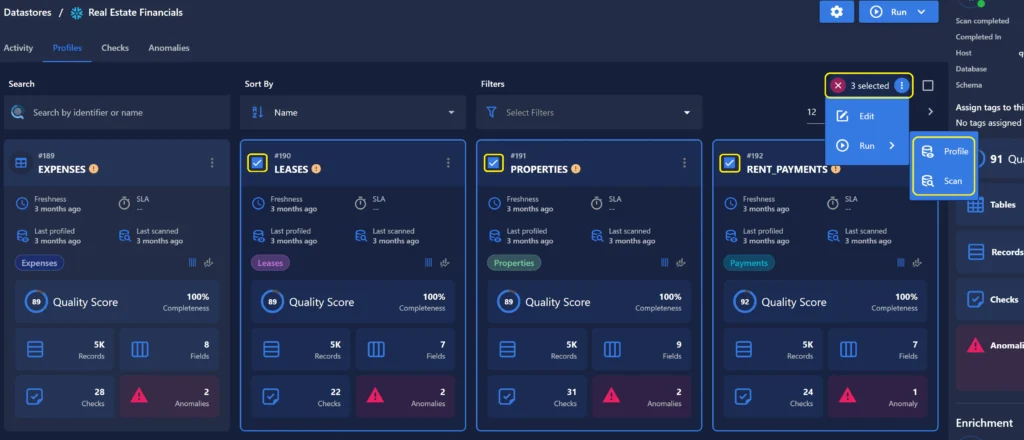
We have expanded our bulk action capabilities to now include profiling and scanning operations.
As usual, our User Guide and accompanying Change Log captures more details about this release.